Creating packer builds with MS Defender for Cloud enabled
General
There are several reason to run private agents for Azure Devops or Github. Honestly, I only have experience with Azure Devops Private Agents, but with regards to the build process, and that is what we are talking about today, the process is exactly the same. If you are using Azure Devops, you probably are used to using Microsoft hosted agents to run your pipelines on. If you are a little bit more advanced, you may also have been using Azure Devops private agents to run your pipelines. There can be several reasons to run private agents, a couple are:
- Using Azure Private Endpoints to integrate, and limit, PaaS offerings to your private network
- You can install custom software, which will be available for your pipelines
- You are able to use specific versions of software, which may not be available in the hosted version anymore
If you are in need of creating your own images for privately hosted devops agents, but you do not know where to start, Microsoft has you covered. The build process for the hosted agents (or action runners, for Github) are made available here, or more specifically for self build images.
Example pipelines for Azure Devops to build an image are available in many sources, but if you want to, I can google that for you.
The problem
However, if your organisation is using Microsoft Defender for Cloud and enabling the servers plan, you can run into issues:
NB: so far I have only noticed an issue on a Windows Virtual Machine image, so if you are not using Windows you are probably fine… 
When you enable this, one of the things that happens is that an Azure Policy is enabled to install Microsoft Defender through the MDE.Windows Virtual Machine extension. Doing this on a (temporary) VM used in a packer build, causes a problem when packer tries to generalize the image by using sysprep: 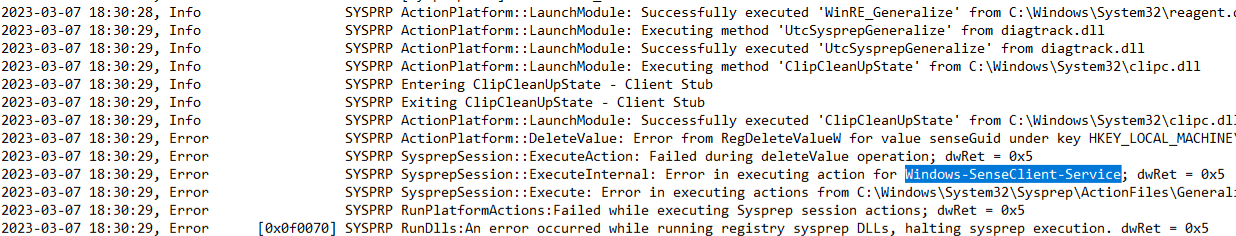
To find what was wrong, I created a VM from the image that was generated and uploaded to the Azure compute gallery in our pipeline. This VM creation process did not complete correctly and when I added the OS disk image as a Data disk to another vm I could retrieve the error above by looking in the “C:\Windows\System32\Sysprep\Panther” folder
The solution
Apparently this is an issue that has been around for a little while. As pointed out by simpleprovider in that article, the solution, or workaround, is to set an Azure Tag in the packer template that builds the VM:
ExcludeMdeAutoProvisioning: True
This prevents the extension from being deployed and thus allows sysprep to complete without an error. This also results in an image that is usable.
For instance, when using the Windows2022 image from the Microsoft github, you can update the “builders” section in the json to include:
1
2
3
"azure_tags": {
"ExcludeMdeAutoProvisioning": "True"
},
Obviously you can include other tags as well…
After including this tag, my build completed successfully.